RFID Tag Cloning
Posted: September 18, 2011 Filed under: Projects 12 CommentsIn the second half of the RFID TTJ episode we covered how to clone or spoof an existing RFID tag. This was partially to expose the security flaws of RFID, but also because it can be very useful. I’ve stayed in a few apartments now that require an RFID tag to get in and out of the main gate. Sometimes you’ll end up getting only one or two RFID tags for the main gate when you have more people living in the same apartment. It’s also inconvenient if you have friends that come over often and you have to let them into the gate every time.
Almost all of this information and work was put together by Micah Elizabeth Scott over at scanlime.org. We simply experimented with the technology and found what works best for us.
At this point, if you haven’t already watched the RFID episode of TTJ, you’ll want to check that out now.
As shown in the video, using the code provided at scanlime.org, you can easily create a clone of an EM4102 (Parallax) RFID tag or a standard HID 125kHz tag.
Although it is shown on scanlime.org that you can clone an RFID tag simply using an AVR ATtiny85 and an inductor, we had a lot of trouble getting this to work well. Our first attempt at this used only the ATtiny85 and the inductor and we were only able to get Parallax readers at very close proximity to detect the spoofed tag. It definitely works, but we wanted to build something that would work from a bit greater range.
For some experimentation, we went to our local RadioShack and found this pack of magnet wire for $7.39. Our plan was to hand wrap a coil:
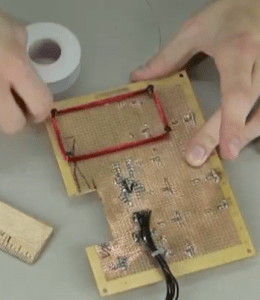
After making a few different coils, we found that the 30 gauge wire and approximately 100-125 wraps gave us the best results. For actually wrapping the coils, we dug out an old perf board that another project had been built on. We found an empty space on the board that was 3″ x 1.5″ and then placed four screws into the board. This then allowed us to easily wrap the coil and simply remove the screws after wrapping. We went with this size because it was close to the existing RFID tag and we were curious how well it would work.
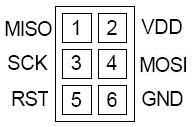
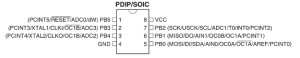
As for programming the ATtiny85, you’ll need some sort of programming cable and something that can act as an ISP programmer (Arduino can do this). For our purposes and in line with the previous RFID post, we used a USBtinyISP. We found a small perf board and wired up the 6 pin header to an 8 pin socket. Below are the pinouts for the ISP programming header and the ATtiny85:
Alright, time to get down to programming. If you haven’t already “acquired” your target tag that you’ll be cloning, you’ll need to do this now. As stated in the video, you can get a Parallax EM4102 tag key by using a Parallax serial RFID reader and anything that can talk TTL serial. For our example, we used an FTDI cable. The easiest way to get data from the FTDI cable is to simply load up the Arduino IDE and select serial monitor. Set your baud rate to 2400 and wave the tag in front of the reader. Write down this value and save it for when we load up the code.
As for getting an HID tag key, you’ll need an HID reader (we prefer the Wiegand version of the MiniProx). We then used an Arduino to connect to our HID MiniProx and get the tag value. Below is a download of our Arduino sketch that explains how to hook up the reader and get the usable site code and unique key that you’ll be entering into the program to be loaded onto the ATtiny85.
The rest of the code loading process is covered in detail in the video. The zip file below contains the source code from scanlime.org, the Makefile, and a text file with the avrdude commands you’ll use to flash the code to the chip. Keep in mind, you will not be able to reprogram the chip again after executing these commands unless you have an external clock source.
If you don’t already have the AVR toolchain for compiling and writing code to AVRs, make sure to grab the software package for your OS:
OS X: CrossPack
Windows: WinAVR + USBtinyISP Driver
Linux: avr-gcc/avrdude from your package manager
Once you’ve loaded up your ATtiny85 with code, pop the AVR out of the socket and wire up your coil to the clock pins (PB3 and PB4 on the Pinout above). For our purposes, it doesn’t matter which wire is connected to which pin. At this point you may wish to neatly pack your ATtiny85 in with the coil and wrap it in electrical tape or use some sort of rubberized coating. Now go try out your new spoofed tag!



I would like to know if there is a way to clone my ez-pass toll tag, I would like to clone my own one so my mother can use it when she goes to work everyday, and avoid having to pay for an additional tag. Please contact me if with any information regarding this, thanks…
Hey Joe,
I can’t say I have any experience with the ez-pass tags so I would have to research it a bit further. At first glance it doesn’t appear to be either the HID or EM4102 RFID tags that I demonstrated in the video.
Eric
There is definitely a way to do it. Someone is running up and down the east coast with me paying their tolls right now. It’s been about $57 of tolls in the past two months from NY, NJ, PA, and DE, and my transponder has never left Maryland. The worst of it is EZ-Pass has no intentions of helping me catch them or refunding my money. They won’t even let me deactivate my transponder until the balance has been used. Now I’m stuck hoping I go through more tolls than the thief does before all the money is gone.
It’s reasons like this that makes me want to work on projects like this… To fully understand the technologies that some companies rely on so heavily for security.
If I get kicked in the ass sometime and these technologies as “proof” I was responsible for something, I want to be able to raise at least a spec of doubt that it may have been a false positive 🙂
Matthew…wow! That’s rough…this is exactly why these companies need to learn to lock down their equipment. I’m really surprised they don’t run into this sort of thing more often. Perhaps they don’t want to admit that their system is fundamentally flawed?
[…] RFID Door Lock RFID Tag Cloning […]
[…] I feel is useful. Although we love using RFID for a lot of our projects, make sure to check out our post on spoofing RFID tags to understand how they can be exploited. Hit up the comments below if you’ve got any […]
is this working with 13.56 mhz cards, too ?
[…] your badge? And what if that code was used to make a counterfeit RFID card with your name on it? It’s possible — but until this long range attack, it hasn’t been practical to obtain the RFID codes […]
can i use that code in the video with this device?
will it still work if you connect a battery to ATtiny85 so you don’t have to set the alarm clock?
If it works is it possible to write another code?
I see a lot of interesting articles on your blog.
You have to spend a lot of time writing, i know how to save you a lot of time, there is
a tool that creates unique, SEO friendly posts in couple of minutes, just type in google – k2 unlimited content